Reporting a Data Breach – How Does it Work?
In a study conducted in 2019, 40% of executives admitted that their company had received concrete indications of cyber-attacks and data theft in the past three years. Experts assume that every company will be attacked sooner or later, or that data of most companies will fall into the wrong hands due to human error. Such an incident can have far-reaching consequences for the affected company as well as for the people harmed by the data breach.
In the first part of our article, we give you information about how to handle an acute data breach. The second part is about preventive technical and organizational measures, which you can immediately implement in your company, to avoid data leaks.
How to Behave in an Emergency: When Must a Data Protection Violation be Reported?
The GDPR requires companies to report data leaks to the data protection authorities and the persons affected. There are exceptions to this obligation, which I will explain below.
Which Data Breaches Must be Reported?
When you think of a data breach, you probably think of hackers trying to penetrate a company network, for example by using phishing software. Social engineering, such as the so-called CEO fraud, is another method often mentioned in the press. These cases exist and they are increasing, but did you know that lost devices also constitute a reportable data breach that has to be reported?
Data protection incidents that have to be reported are, for example:
- Loss of equipment, on which personal data was stored
- Login data has fallen into the wrong hands
- Confidential information was sent to a mailing list
- Instead of BCC, CC was used and recipient lists can be viewed
- Data has been deleted by an unauthorized person
- Blackmailing software has infected the company network
- Tricksters have gained access to confidential information (for example, by intruding into the building, flirting or making clever telephone calls)
To Whom Must a Data Breach Be Reported and What Is the Deadline?
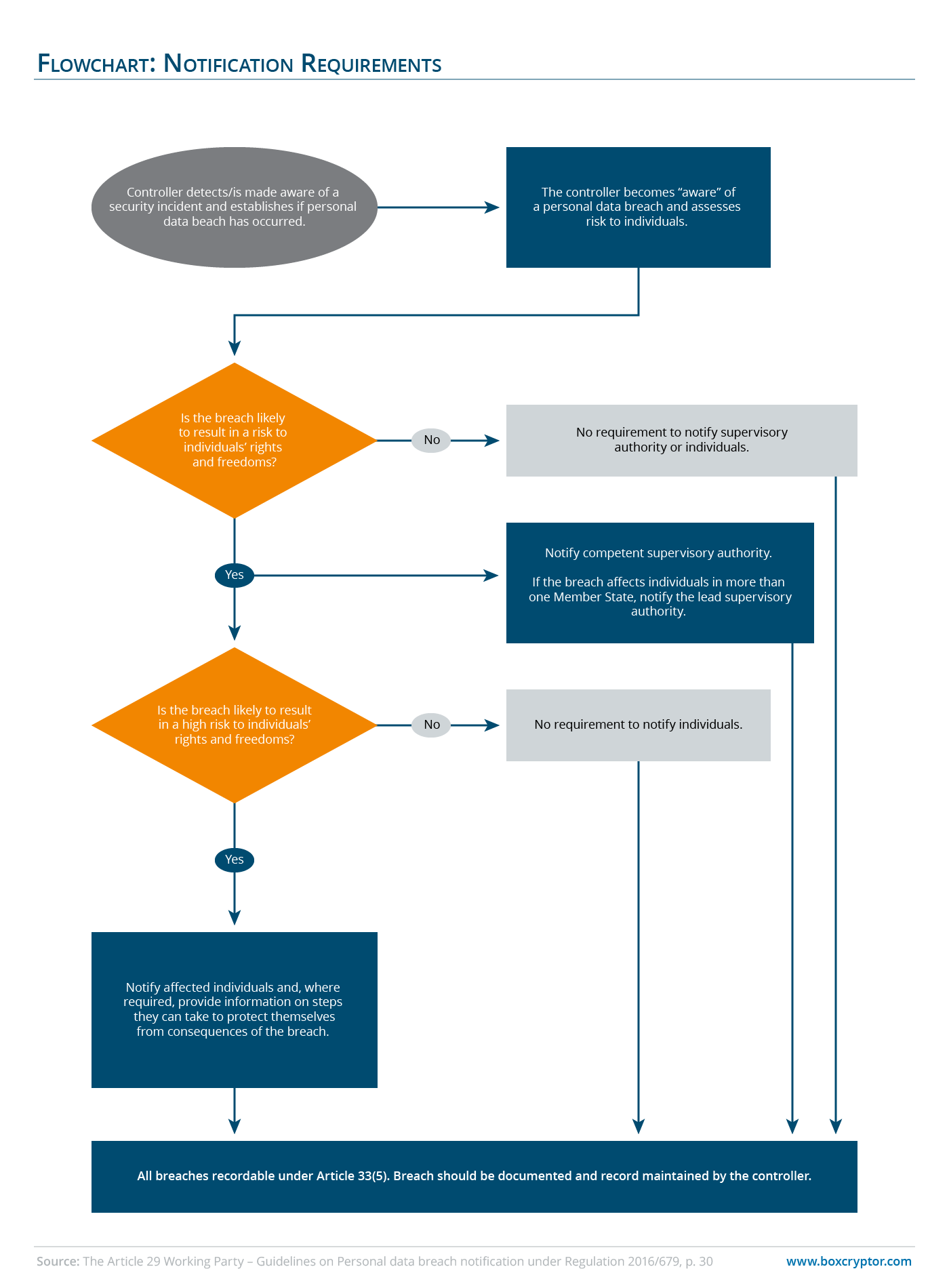
Data protection authorities must be notified within 72 hours after becoming aware of a breach. If the data leakage could lead to “a risk to the rights and freedoms of individuals”, the data subjects must be informed immediately.
The following information must be communicated to the data protection authority:
- Description of the nature of the breach, indicating – when possible – the categories and approximate number of data subjects, the categories and approximate number of personal data sets concerned
- the name and contact details of the Data Protection Officer(s) or other contact options for further information
- Description of the likely consequences of the breach of the personal data
- record of the measures taken (or proposed) by the controller(s) to remedy the breach of the personal data, and – where appropriate – measures to mitigate its possible adverse effects
The purpose of this documentation is to enable the supervisory authority to verify compliance with the provisions of Article 33.
Notification of Persons Concerned
Notification of data subjects must be given if the data leakage could lead to “a risk to rights and freedoms”. For this reason, the obligation to inform must be complied with immediately. Depending on the seriousness of the incident, consultation with the data protection supervisory authority and, if necessary, with the law enforcement authorities may be necessary.
The notification must be made in clear and simple language. It must contain a description of the nature of the data breach. And it must contain recommendations for mitigating any effects, for example, a notice that passwords should be changed.
Which Data Protection Supervisory Authority Is Responsible for Which Company?
In general, the competence of the supervisory authorities depends on the location of the company to be supervised. Apart from the supervisory authorities, that are responsible for specific regions, there is the general Data Protection Authority (DPA). If you have a breach to report (Art. 33 DS-GVO) and your headquarters is within the EU, you can either contact the DPA (Data Protection Authority) of your country, or the Data Protection Supervisory Agency of your region.
In Germany, for example, the state data protection authority of the respective federal state is the first point of contact for reporting a data leakage under the GDPR.
My Company Is Based Outside the EU: Where Do I Report a Breach Affecting EU Citizens?
If you are based outside the EU and you have a data breach concerning EU citizens, you are also bound to report the breach to EU Data Protection Authorities, according to article 3 (2) GDPR.
GDPR applies to the processing of personal data of data subjects located in the Union by a controller or processor not established in the Union if the data processing is related
(a) offer goods or services to data subjects in the Union, whether or not payment is required from those data subjects
(b) to observe the conduct of data subjects insofar as their conduct takes place within the Union.
A jurisdiction is established if the processing activity is directed at persons residing in the respective EU Member State (Recital 122: competence of the supervisory authority). An "orientation" is to be assumed if the data processing is intended to provide goods or services to data subjects in the Member State or to monitor them. The consequence is that several supervisory authorities may be competent.
Vera Franz, lawyer, specialist in IT law, Schmid Frank Rechtsanwälte PartG mbB
For companies without a location or branch offices within the EU, only Art. 55 DS-GVO applies.
If the company has at least one establishment in the EU and cross-border processing operations take place in different Member States, the so-called One-Stop-Shop procedure applies. The intention is that only one supervisory authority is "in charge". This way, companies do not have to deal with potentially divergent decisions of different supervisory authorities.
According to article 27 of the GDPR, companies that handle data of EU citizens have to name a representative inside the EU. In case of a data breach, report it to the DPA of the country, where your representative is based. Here is a list of the DPA’s of the different EU countries.
When Does the Obligation to Report Cease?
The obligation to report data protection incidents ceases to apply as soon as one of three conditions occurs:
- if immediately after the data failure it was ensured that the risk for the persons concerned no longer exists (for example, if a lost device can be deleted remotely)
- if technical and organisational measures have been taken to prevent access by unauthorized persons (for example end-to-end encryption of communications and cloud storage)
- if a notification of the persons concerned would be too much effort (the data protection supervisory authority must be notified, nevertheless).
This flowchart will help you make a decision, concerning the obligation to report a data brech
Preventive Measures 1: Prepare Employees for the Emergency
In principle, it is always advisable to establish a corporate culture that is sensitive to data protection. This means that all members of the company must be included. Two goals are important here:
- employees have the motivation to want to be “safe”.
- employees have the competence to make the right decisions.
Unfortunately, this ideal scenario is difficult to achieve. The reason is that employee training usually addresses the analytical system in the brain, but phishing emails and ransomware target the systems of fear and boredom – and thereby often succeed. It is therefore necessary to rethink how employees are sensitized to IT security.
Linus Neumann made various suggestions at the 36th Chaos Communication Congress, which took place at the end of 2019. According to his experience, a learning experience can be achieved primarily by setting up phishing traps in one’s own company and addressing employees specifically with emails. All those who fall for the attack and, for example, reveal their password, can then be educated with a video. Such measures are relatively successful, but, unfortunately, they do not have a long-term effect, which is why they must be repeated regularly. It is also important to vary the attack scenarios. Employees who successfully ignore phishing emails may still plug a USB stick into their computer when they find it in the car park.
The quality of the communication with the IT department should also not be underestimated. If employees have fallen victim to phishing, the IT department must be notified, because a quick response can often prevent greater damage. It is therefore necessary that the IT department encourages and rewards reports.
Preventive Measures 2: Set Up Technical Security Measures
On a technical level, there are also a number of preventive measures that can reduce the risk of data breaches:
- The principle of least possible access: Employees should only have access to the files they need for their work. User rights are assigned as sparingly as possible.
- Different areas of the IT infrastructure are sealed off from each other: Production servers or office infrastructure should not run on the same network as the office computers. VLANs are a good option.
- Particularly sensitive data should be stored separately from other data.
- There are defined processes for sensitive processes (bank transfers, data transfer, etc.).
- The use of password managers is mandatory. This way, self-created passwords that are easy to remember and that are used several times can be avoided.
- Security processes should not be mapped by email or in the browser.
Discovering Data Leaks
On average, hackers need two hours to move through the IT systems and cause damage in case of an attack. When they work in groups, they can even start causing trouble in less than 30 minutes. Considering that companies in Germany need about 11 days to react to such an attack, it becomes clear how much more action is needed in this regard. Internationally, the reaction time is 7 days, but that is still far too long.
Ideally, an attack on the network is detected within a very short time by automatic monitoring of the systems, and interrupted as quickly as possible. A short reaction time is a big challenge for most company structures. But still, the rule is clear: react as quickly as possible.
Practice Makes Perfect: Have a Test Alarm
Similar to a fire protection plan or a fire alarm exercise, it is advisable to play through the reaction to a data Breach. A standard process helps optimize the coordination between the IT department, the legal department, and the data protection officer(s). A checklist should be an integral part of this strategy.
Larger companies should consider setting up an interdisciplinary Data Breach Incident Team. Such a team will be available at short notice and is specialized in reacting to data breaches. It also makes sense to call in an IT lawyer or specialist solicitor and coordinate with the PR department – depending on the severity of the data breach.
The contact details of these people and a checklist should be available on paper so that they can still be accessed even if the IT infrastructure is completely shut down. Some computers that are not connected to the company infrastructure could ensure the operational capability of this team in an emergency.
Conclusion
Data breaches cause great damage in companies. As digitalization progresses, the risk increases if companies do not consider IT security at every step. With preventive measures and an awareness of the relevance of IT security, you can reduce this risk enormously. If you should still be affected, stay calm and react quickly. If you fear fines according to the GDPR: You do not necessarily have to, when you do not deliberately handle sensitive data negligently. Even in the event of a data breach, you have little to fear if technical and organisational measures have been taken in advance, and you react quickly and cooperatively, when the incident becomes known. If you need support in securing your data in the cloud, we will be happy to assist you.